How HTTPS works – SSL/TLS ?
What is HTTPS ? Why do we need it and how does it works? What is SSL/ TLS? Today we’ll be covering all the essentials of HTTPS that every developer must know.
Introduction to HTTPS :
As we all know, HTTP is the most common protocol used for the web-based communications. As the data travels over the network through different routers and your ISP server, it is susceptible to threats like MiMT(Man in the Midde Attack) which might lead to eavesdropping or potentially data tampering. The growing needs of moving data securely over the web gave rise to the use of HTTPS.
Most of the websites which involve critical user data communications like Gmail, Twitter, Facebook, shopping and banking websites always makes use of HTTPS protocol. Moreover, nowadays even many blogs and news related websites are all switching to HTTPS.
HTTPS ensures the following needs for secure communications are met :
- Confidentiality : HTTPS maintains privacy of all communications over web using cryptographic encryption(symmetric as well as asymmetric is used, we’ll see how.). It prevents eavesdropping.
- Integrity : It prevents intruders from tampering the data being communicated over the channel.
- Authenticity : It makes use of Public-Private Key Infrastructure to enable you to make sure that entities are who they say they are.
In HTTPS, the network security is provided by TLS(Transport Layer Security) protocol.HTTPS is often referred to as HTTP over TLS or HTTP over SSL.
Let’s understand SSL and TLS in detail and how they work.
SSL vs TLS :
In all your communications about HTTPS protocol, you’ll get to hear a lot about SSL or TLS. Both SSL & TLS are the transport-layer protocols(Actually they are not, but they are thought to be standing at that level in OSI Model) which are used for securing data communications over web. TLS/SSL aims to provide confidentiality and data integrity for network communications. Although, TLS and SSL are the terms used interchangeably, still they are both different. Let’s first look at the differences.
| SSL | TLS |
|---|---|
| stands for Secure Sockets Layer(SSL) | stands for Transport Security Layer(TLS) |
| Developed by Netscape and launched in early 90's. SSL 2.0 was launched in 1995 and then SSL 3.0 in 1996. | The TLS was first defined in 1999 as an upgrade of SSL 3.0. The TLS 1.1 was later defined in 2006 , 1.2 in 2008 and then came TLS 1.3. |
| The 2014 POODLE Attack was marked as a SSL's death knell. | TLS can be thought of as a successor of SSL, after the SSL's death. |
| SSL is now prohibited of use by IEFT(Internet Engineering Task Force). If you hear of this term being used, it usually refers to TLS. | TLS is used for HTTPS implementation as of now. If your boss tells you to implement SSL, he might be referring to TLS. |
How TLS Works?
Each new TLS connection involves a handshake between the server and client.
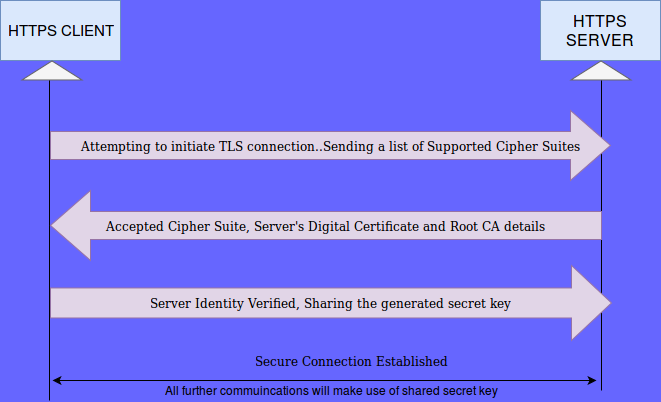
- Client request a secure TLS connection to a TLS – enabled server and sends a list of cipher suites(ciphers and hash-functions) it supports as part of this request.
- Server picks a cipher and hash-function, the one it supports, from the passed-on list and notifies the client of the decision.
- Server also share its digital certificate along with the root CA details and its public key.
- Client verifies and confirms the server’s identity using the digital certificate presented to it.
- A session-specific shared secret key is generated by the client by encrypting either some random number or the output of Diffie–Hellman key exchange algorithm using the server’s public key. This encryption of shared secret key using server’s public key ensures the confidentiality of the shared secret key.
- Client shares this generated session specific secret key to the server.
This completes the handshaking process which is achieved using a Public Key Infrastructure(yet to cover). For the rest of the session, both the client and server use this session-specific shared key for all communications(symmetric communication).
Symmetric Key Encryption :
This is a very simple cryptographic algorithm which makes use of a common key for both encryption and decryption of the message digest. The two parties mutually agree to use a common shared secret key for all their communications. The sender encrypts the data using the shared secret key and sends over the network. The receiver on receiving the message decrypts it using the same shared secret key.
Public Key Infrastructure(Asymmetric) :
In this type of cryptographic framework, both the involved parties has a public and a private key. Public keys may be disseminated widely but the a private key can be thought of as a secret key which should only be owned by the owner and must be protected at all times. Rather, private key and secret key are the two terms used interchangeably.
There are two best known uses of this cryptographic system :
- Public Key Encryption : The sender encrypts the message using the receiver’s public key and that encrypted message can only and only be decrypted using the private key which only the receiver holds. It maintains data confidentiality.
- Digital Signatures : In this process, a message is signed by a sender using his own private key and is sent over the network. It can be verified by anyone who holds the sender’s public key(of course, which is public in nature). However, it ensures that the message is coming from a specific sender as it holds his digital signature thereby catering the authenticity requirement.
The Public Key Cryptographic systems rely on the algorithmic mathematical problems for which no efficient solution is known till date, thereby making it difficult for the intruder to break-in through the system.
Digital Certificates :
Digital certificates are issued to the users by a CA(Certification Authority). CA acts as a centre of trust to help other users to verify the client’s digital certificate. There are different available CAs which can issue the certificate like VeriSign, Entrust etc.
For you to receive a digital certificate from a CA, you are expected to submit a CSR(Certificate Signing Request) to the concerned authority. CSR is generated using your public key. On completing your identity verification process, the CA signs the certification and issues it to you.
CA holds the right to revoke the certificate at any point of time, in case a user is found guilty.
Conclusion :
HTTPS Protocol is a means of having secure communications over web. It can be thought of as HTTP over TLS or HTTP over SSL.
TLS/SSL are the protocols which ensure the data confidentiality and integrity functions are met. It also provides an optional authentication function to verify identity of either a client or a sever or both(usually the identity of least one party, mostly server, is always verified). The authentication process involves use of digital certificates signed by a trusted CA(Certificate Authority).
To receive a digital certificate, a CSR(Certificate Signing Request – generated from the public key) needs to be submitted to the CA. The digital certificate is issued to the user after the identity verification process is completed by the CA.
HTTP uses the TLS/SSL tunnel for the communication which makes use of both symmetric and asymmetric (Public Key Infrastructure) cryptographic algorithms.Firstly, a TLS handshake is performed between the client and server to agree on a cipher suite and a session-specific shared ‘secret key’ using Public-Key Infrastructure. On completion of TLS handshake, the server and client use the same shared secret key(symmetric key) for both encryption and decryption for all remaining communications within that session.
